Mobile app development companies are not yet entirely prepared for repercussions of wandering into the digital space, and consequently, the more we move into the digital world, the more we risk losing our real world.
Also, when we say the real world, we mean the personal and other forms of data that we generate through mobile apps in our day-to-day interactions with the real world.
At present, Mobile device security/cell phone security lies on top of every company’s worry list these days. Smartphones have the same security flaws as additional internet-connected devices.
And the good thing is nearly most of the people will daily access corporate data from; it means keeping sensitive info out of the wrong hands is an increasingly intricate puzzle.
Not just that, even the professional aspects of life as well have been influenced quite much by the digital revolution, especially since corporations have encouraging Bring Your Device (BYOD) policy.
Then a personal and professional data that we carry in our devices all the time are at obvious risks from security threats. Some of the security risks are obvious to cover, but some are not what we usually expect to face.
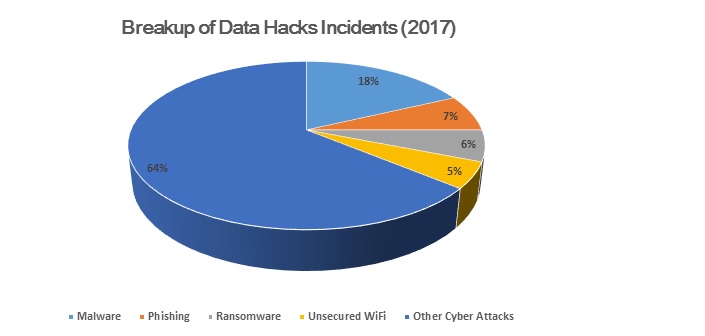
The malware currently ranks as the least collective initial action in data breach incidents. In fact, coming in behind even physical attacks in Verizon’s 2019 data breach report.
So better say thanks to both the nature of mobile malware and the inherent protections built into modern mobile operating systems.
Data leak or hack attacks are significant threats to our data, but then some risks are not even noticeable but steal or swipe data from phone storage.
There are many ways that hackers adopt to invade our phone’s internal storage to look for personal, media, or sensitive information.
In this article, let’s take a look at the most common ways security threats that smartphone users face and how they can avoid a security breach in their phones:
1 . Unsecured Wi-Fi connections
When you connect to an unsecured or untrusted WiFi connection, you are indirectly providing the source with an opportunity to access your smartphone. Usually, users in a café, airport or other public places, login to an open WiFi network assuming that the source must be owned by the place they are at. And usually, that is the case. But security breach is not something that you come across every day, and it is very much possible on one bad day. Technically, when you use an open WiFi network, the data that you transmit over the network during chatting, internet banking, emails etc., can always be intercepted and decoded by malicious entity and can be used in accessing sensitive information. Some of the common ways hackers may use WiFi to access your phone are Man-in-the-Middle attack, Side Jacking, and more. An obvious tip to avoid this kind of attack, make sure you connect to only trusted WiFi networks, public or private.
No one is ready to burn their cellular data when wireless hotspots are available, but the things are free Wi-Fi security systems are weak.
When you connect to an unsecured or untrusted Wi-Fi connection, you are indirectly providing the source with an opportunity to access your smartphone.
Usually, users in a café, airport, or other public places login to an open Wi-Fi network, assuming that the source must be owned by the place they are at. Besides, usually, that is the case.
But security breach is not something that you come across every day, and it is very much possible on one lousy day.
Technically, when you use an open Wi-Fi network, the data that you transmit over the web during chatting, internet banking, emails, etc., can always be intercepted and decoded by the malicious entity and can be used in accessing sensitive information.
Some of the common ways hackers may use Wi-Fi to access your phone are Man-in-the-Middle attack, Side Jacking, and more.
An obvious tip to avoid this kind of attack make sure you connect only to trusted Wi-Fi networks, public or private.
And never use free Wi-Fi to access personal or confident services like banking or credit card information.
Also Read: Top 10 Threats in Enterprise Mobile Security and How to Mitigate Them
2 . Phishing
Phishing is another one of the wicked ways in which hackers can fetch much more than your generic data.
Because mobile devices are always powered-on, they are the front lines of most phishing attacks. According to a report, mobile users are more vulnerable because they are often monitored their emails in real-time, opening & reading emails when they received.
The security threat level of Phishing depends upon the kind of data the hackers are trying you syphon off your hard disk.
Phishing is a type of cyber-attack that includes an email disguised as something useful to you so that you are tempted enough to fall for the clickbait.
Usually, a simple website is replicated and inserted in the link within the email.
The link that you click on takes you to a webpage embedded with a particular type of script, coded to steal your credentials.
The best way to avoid Phishing is to identify phishing emails. Most phishing emails are usually identifiable. Check for parts in the URL that look incredibly fake.
For example – if your account is in let’s say, HDFC Bank, and you receive an email with URL something like – hdfc@secure.com or securecode@hdfc.com, you can spot how the attacker is trying to get you in confidence by adding the word secure to the URL, just so that you think it is ‘safe’ to click.
You may also get a mail that says you have won some reward, and to claim it, you need to visit the link provided in the mail. So always check the link before you follow it.
And if the matter isn’t urgent, then let the response or action items wait until you are at the computer.
Recommend: Trends that will boost the future of mobile app development
3 . Malware
There is a reason why Google Play Store and App Store recommend downloading only from them because you download an app from an external app store, chances are you may unknowingly download an app, which is spyware – a type of malware that collects and sends over your personal information to a malicious server.
Here is a graphical representation of what Nokia stated in its malware report 2017.
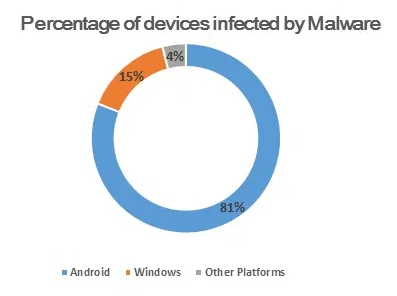
Some of the apps will not even ask for permission and discretely steal data in the background. Recently, a malware called ‘Android Trojan,’ which is a Hidden Miner malware has been detected. It is infamous for taking personal data from some of the popular social media and other apps like Facebook Messenger, Skype, WhatsApp, and many other apps for communication.
Most of the malware apps are immediate downloads that install the Android Package file on your phone, disguised as the app you were looking to download.
So, if you want to take the least risk, then do not download from anywhere other than the official application distribution stores.
However, in case, you want an app that is not available in the mobile applications market, check the filename and download preview before you start the installation.
However, the key to avoiding these security threats by a clear margin is to check what you are downloading even from the official application stores, as not even the official app stores have a foolproof strategy to check malware apps.
In mid-2017 Android security is under threat, Google Play Store admitted its inability in handling malware applications and releasing a shocking figure of 21.1 million Android devices being affected by malware apps that were download from Google Play Store.
Notably, this one was one of the most massive malware outbreaks in the world, which surpassed the Google Play Protect.
One of the most common malware among the wave was ExpensiveWall, which uses the user’s SMS and premium services on the phone and worked in the background without letting the user know.
Recommend: How mobile app development companies are helping businesses build brand image?
4 . Data Leakage
Mobile is often the cause of inadvertent data leakage.
For example, take ‘riskware’ apps, which create a problem for mobile users who grant them full permissions, but they always do not check the security.

You can find these apps in official app stores that perform as advertised but also send personal & potentially corporate data to a remote server, where advertisers and most of the time mine it by cybercriminals.
Another way of data leakage is though hostile enterprises signed mobile applications.
These mobile malware programs use distribution code native to popular mobile operating systems such as Android & IOS to move valuable data across corporate networks without raising red flags.
To save from these kinds of mobile data security issues, only give apps permission that they needed for proper functioning. And steer clear of any apps that ask for more than necessary.
In September 2019, Apple IOS and Android security update protocols to make users more aware of it and why apps collect user’s location information or data.
Recommend: How helpful is a mobile app in a growing business?
5 . No password hygiene
With all of the ways to secure mobile devices, it might be outrageous to know that 34% of people don’t opt for a password to lock their phones.
In such cases, if these devices are stolen or lost, it gives hackers or thieves easy access to all the info stored on the phone.
Even though people create a password, they won’t put more interest or care on creating a password or PIN; they typically default to codes that are easy to crack or break, such as 1234, date of birth, 0000,1111, and many more.
Top 10 worst passwords of all time:
123456
123456789
Qwerty
Password
I love you
11111111
123123
Abc123
Qwerty123
Admin
Source: Security magazine
Unlike websites, mobile devices won’t force users to create a pin or password. Even though they created the pin, they will not check the strength of the password.
To be safe from this type of mobile security threats, ask your employees to follow identity access management roles or requirements to them when they are using their own devices to access the company data.
Taking it further, allow them to login with 2-factor authentication while accessing internal tools.
6 . Lack of end-to-end encryption
A recent study revealed that only 5.5% of mobile application development budgets spending on security.
You might be shocked after considering the amount of information uploaded to apps. Contingent on the platform employees use to access corporate information/data on their phones, a lack of mobile app security does not bode well for you.
Daily you will send and receive tons amounts of data, so leaving that unencrypted leaves the door open for outsiders at what is being done or said in your organization.
Apart from hackers, many more people will have access to information such as conversation hosts or third parties.
To be saved from this thing, use communication apps that encrypt data transfers to make sure that communication between your employees and you cannot access by anyone outside of the business.
Therefore, it is better to go for encryption-based applications to help manage communication.
Recommend: How to improve app usability & its conversions rate?
7 . Inactive apps
Every year will google play store, and the Apple app store will remove many apps. But the thing is most of us don’t understand why it is happening? And even they don’t give any explanation too.
We can imagine that these occasional purges have something to do with privacy breaches and security threats.
In Google’s case, they found apps that forced users to click on the ads by making it hard to use the app otherwise.
When a handler clicks on the ad, it runs in the background without user permission, while the ad accumulates automated clicks to generate income for the app developer.
How to deal?
It is good to have transparency between users and enterprises, so they know what apps could threaten their devices. You and your organization employees should be proactive and regularly check the apps on the devices to see if they are still active.
If the apps are not active, it’s better to remove them from mobile devices.
Recommend: Essential features of an app which app developer cannot miss
8. IoT mobile security threats
Mobile devices are growing from cellphones & tablets to include wearable tech, such as devices or smartwatches in organizations like video conferencing tools.
Fundamentally, anything that is used to enhance workplace efficiency, service quality, and productivity has a product for that purpose.
One important thing to remember is cyber attackers or cybercriminals are aware of these advancements. And Gartner revealed in their study that, number of connected devices would reach 20.8 billion by the end of 2020.
Because of this, mobile security shouldn’t just be about the data and the network; it should spread to comprise securing the devices/gadgets.
How to deal?
The best practice to deal with this type of threat is to educate your employees on where threats can come from and how to use the devices safely.
So take mobile security seriously because threats can come from almost anywhere.
Recommend: Top 4 predictions of the internet of things in 2019
- Final words
Something to be remembered always is that mobile app development is a boon for the digital world, but it is not entirely free of negative consequences.
Keeping your smartphone safe is not that difficult if you follow the generic instructions and roam besides, far from what Android and iOS developers suggest, i.e., download from just the official app stores.
Apart from that, another way to keep your smartphone intact from security threats is not to visit the website or follow links you do not trust as most of the time, what we authenticate accidentally could cause a lot of damage to our digital privacy.
I hope you got a better understanding of security threats and how to deal with them.
If you still feel any more mobile security threats to need to add for this list. Please provide in the comment section.


